Following AWS security best practices when hosting your applications is vital to increase cloud security, privacy, and control network access. Because let’s be honest: How long do you think your app will survive without securing legitimate access to it?
Everybody is concerned about their information and its safety and security, especially sectors like banking and finance, which have stricter rules about data storage, residency, and sovereignty. So, keep reading to discover the AWS security best practices every financial service must follow.
- How Does AWS Security Work?
- Common Challenges in AWS Security
- AWS Architecture for Fintech Applications Video
- Panorama of the Security Risks in Financial Services
- Top 10 AWS Security Best Practices
- AWS security Case Studies for top FSI customer
- Conclusion of AWS Security Best Practices
- FAQs
How Does AWS Security Work?
As a leading cloud provider, AWS has to ensure secure data protection, infrastructure, and systems. Therefore, it operates on a shared responsibility model, where AWS manages the security of the cloud infrastructure.
At the same time, clients are responsible for securing their data, applications, and configurations within AWS services. This collaborative approach provides a robust security posture for AWS-hosted environments.
Common Challenges in AWS Security
Now that you know that security is a shared responsibility in AWS, users must take responsibility for access control, audit logging, monitoring, etc. This can ensure the company can pinpoint the exact problem by analyzing the logs if something goes wrong within the AWS environment.
Even if AWS provides a certain level of protection, it simply cannot cover every aspect of security compliance. Analyzing yourself is essential to ensure you don’t leave yourself exposed to attackers.
Example
If you have plaintext credentials in environmental variables, AWS can do nothing for you. You have to ensure you are not using credentials in plaintext format for your applications.
The following are some challenges of using the cloud for application deployment.
- DDOS and DOS Attacks
Distributed Denial of Service(DDOS) or Denial of Service(DOS) attacks affect the functioning of applications by overwhelming the website servers so that they can not respond to legitimate or valid user requests. This can result in loss of reputation, brand, and revenue too. - Data Breaches
There is a risk of data theft while storing critical or business data on the Cloud. A data breach can be intentional or unintentional and is attributed to hacking or malware attacks. - Data Privacy or Data Confidentiality
It is one of the major concerns for financial service industries when using the cloud to store their data. On the one hand, it has its advantages. On the other hand, there are concerns related to data breaches, data privacy violations, and penalties by data protection regulations for data security failures. - Sharing of Resources
Cloud is designed to share hardware resources like Memory, Storage, and CPU. While this looks pretty easy, it also has its security issues. This makes it difficult for organizations to ensure that the data is accessed by authorized people only and is not available to others.
AWS Architecture for Fintech Applications Video
Panorama of the Security Risks in Financial Services
57% of banking executives recognized cyber security as a top priority in 2024, according to FORTRA.
Cyber Criminals usually target Financial Institutions and are at greater risk than other businesses. Banks’ sensitive data could be at risk if the security is compromised, which can cause heavy financial and reputational damage, leading to heavy losses and data theft.
In common attacks, the unencrypted data stolen by attackers can be misused, dragging financial institutions into serious problems. This is not always the case; data may not be stolen but changed sometimes by attackers. This altered data can be challenging to identify and cause financial institutions to incur millions of dollars in damages.
In some cases, compromised end-user devices like mobile phones or computers used to connect to banks can transfer malware that could attack banks’ networks.
To safeguard financial institutions or any other organizations from such risks, intrusion detection or intrusion prevention systems are commonly used, and they play a vital role in identifying potential attacks on the systems. Intrusion Detection is a strategy that organizations must consider to protect network environments from hackers. It is an ability to monitor and react to application or system misuse.
Organizations must also have an automated process like vulnerability scanning to identify networks proactively. It is an essential step for Financial Organizations or any other organizations towards hardening security defenses.

Top 10 AWS Security Best Practices
In a Cloud Platform like AWS, there are services used for multiple purposes like storing data, accessing productivity tools, and deploying IT infrastructure. In all these use cases, cloud services allow organizations to move faster. However, the use of any cloud service or AWS comes with challenges and risks to data security.
These AWS Security best practices show you how to lift, shift, and operate your business on the cloud.
In the following steps, we’ve outlined best practices to guide Financial Service Industries toward a secure AWS Cloud and address AWS Cloud Security issues.
Read our blog, AWS Benefis, to get the most out of the Cloud.
AWS Security Best Practice 1: DevSecOps Adoption
DevSecOps is a relatively new term. It introduces security in the Software Development Life Cycle (SDLC). DevSecOps is a collaboration between DevOps’s Development and Operations teams, including security teams. In short, DevSecOps is a shared responsibility, and everyone involved in Software Development has a role in building security into the DevOps workflow.
There are three basic steps in DevSecOps to securely do continuous integration and continuous deployment.
- Insert codified and automated security checks in the software development and operations.
- Implementing policy and practice to ensure code freshness as a fix for a vulnerability is available in the most recent software version.
- Identify flaws and mitigate them as early or fast as possible.
Veracode helps to secure software development and testing before moving to production and provides dynamic and static code analysis to detect vulnerabilities and reduce risks. It reviews the source code and performs quick checks before a release covering web applications, mobile apps, and microservices.
Veracode Static Analysis provides automated security feedback to developers in the IDE. The CI/CD pipeline conducts a Scan before deployment and gives clear guidance on finding, prioritizing, and fixing issues.
AWS Security Best Practice 2: Security Automation
AWS WAF is a Web Application Firewall that helps protect applications hosted on AWS Cloud against common web threats that can affect the applications’ availability and security, consume infrastructure resources, and lead to slowness and increased resource usage.
WAF can also automate security using AWS Lambda to analyze weblogs, identify malicious requests, and automatically update security rules. AWS WAF can protect against Cross-site scripting attacks, SQL injection attacks, and Attacks from known wrong IP addresses.
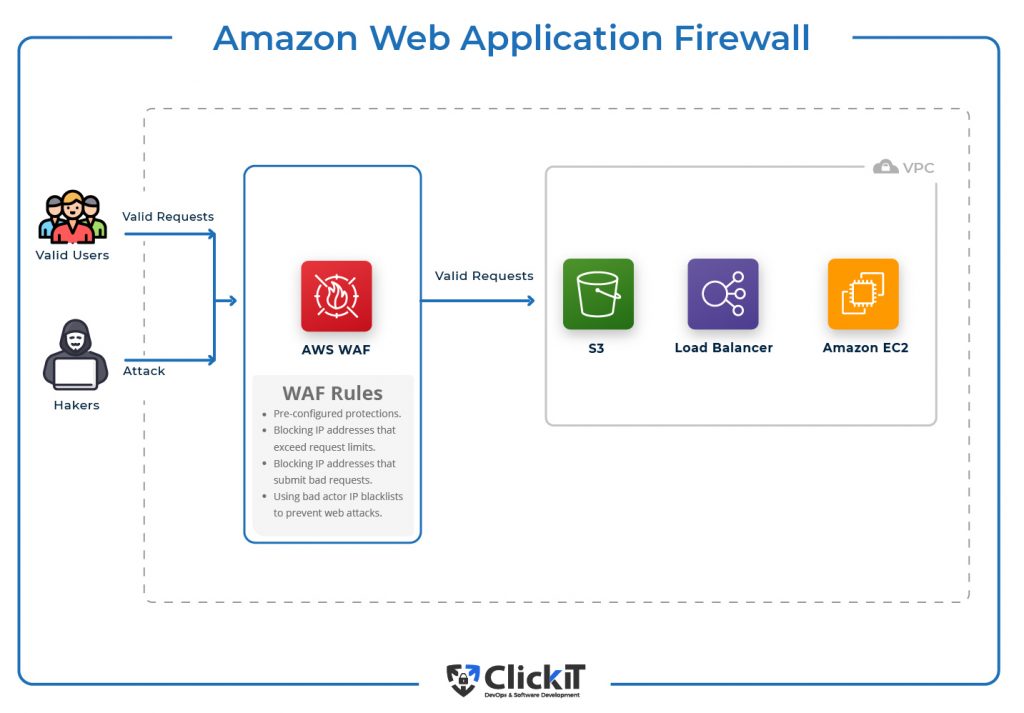
Example
The diagram shows that valid requests are forwarded to your application deployed in the VPC, whereas requests from the Hacker that match the WAF rules are blocked. These rules can be a pre-configured template to quickly start with AWS WAF, a set of IPs that exceed request limits and can cause HTTP floods and IPs that can generate bad requests.
AWS Security Best Practice 3: Implement Security Groups
Security Group acts as a virtual firewall for EC2 instances on AWS Cloud to control inbound and outbound traffic flow and provides Cloud Security.
Security Groups operate at the instance level; each instance can have up to five AWS security groups attached. You can not block incoming traffic; you can only allow it at a particular or range of ports.
Security Groups are stateful, and you do not need to add rules for return i.e. a rule that allows traffic into EC2 Instance will automatically allow responses to pass back out from the EC2 instance.
Example
If you allow connection on port 22 from a particular IP, that IP will be able to connect to the EC2 instance on port 22. The connection will also be automatically allowed to flow out from the EC2 instance via port 22 on that allowed IP.
AWS Security Best Practice 4: Activate Threat Detection Systems
In this AWS security practice, Guard Duty is an intelligent, cost-effective option for continuous threat detection on AWS Cloud. Guard Duty uses machine learning, anomaly detection, and integrated threat intelligence to identify and prioritize potential threats.
With a few clicks, one can enable Guard Duty in the AWS account to continuously analyze network, account, and data activity. Guard Duty analyzes DNS Logs, VPC Flow Logs, Cloudtrail S3 Data Events, and Cloudtrail Management Events.
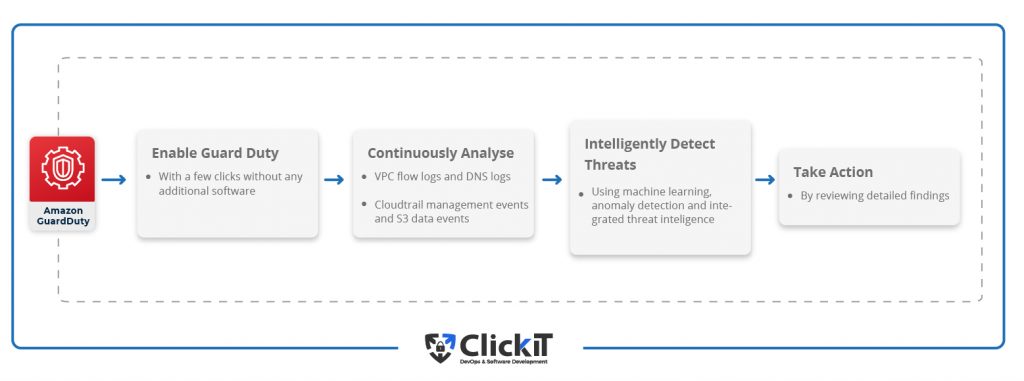
Example
Suppose you have your Banking Application deployed in AWS and S3, EC2, RDS and, a few of the services that you are using. In that case, unusual Amazon S3 discovery API calls, unauthorized creation of new IAM users, roles, or access keys, resource hijacking of Amazon EC2 instances, generating Amazon RDS snapshots are a few of suspicious behavior the machine learning model of Guard Duty can now help you detect in your account.
AWS Security Best Practice 5: Improve Compliance of the App
AWS Inspector is an automated security assessment service. It helps to improve the compliance and security of the applications deployed.
It automatically assesses applications for vulnerabilities, exposure, and deviations and produces a detailed report of security findings prioritized by severity level. Amazon Inspector checks for unexpected network accessibility of EC2 instances and vulnerabilities on those EC2 instances.
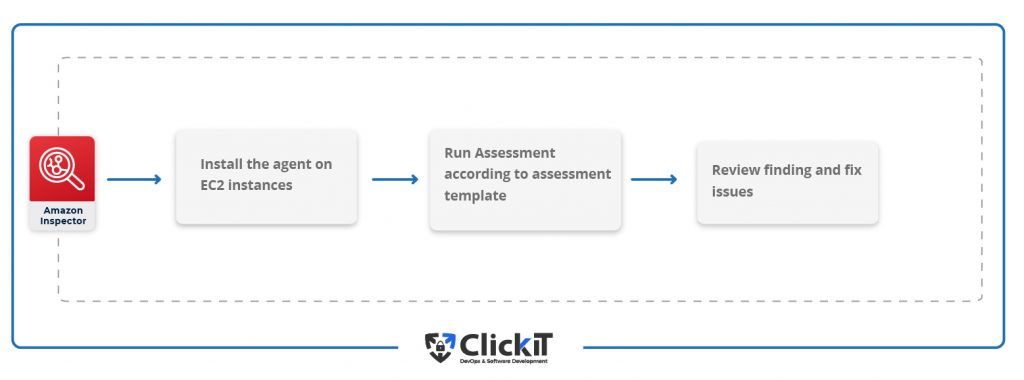
Example
Governments enact several regulations at a local and national level when it comes to the financial sector, which can be challenging to identify. In this case, Amazon Inspector can come to the rescue by enabling scheduled vulnerability scan audits periodically. This can give confidence to the organization to say that they are adhering to the best practices and regulatory requirements.
AWS Security Best Practice 6: Monitor your AWS resources
In this AWS Security practice, we recommend being alert to your AWS environment and resources by embracing robust tools like CloudTrail and CloudWatch.
CloudTrail
CloudTrail simplifies compliance audits by automatically recording and storing event logs for actions made within the AWS account and increasing visibility into your resource and user activity.
Cloud trail enables compliance, governance, operational auditing, and risk auditing of the AWS account. It simplifies functional analysis and troubleshooting.
Example
If you have enabled Cloudtrail in your account, you can track account activity within an average of about 15 minutes of an API call. If you are unsure of the owner of the resources created in your account, you can check the trail, learn about it, and take the appropriate action to help.
CloudWatch
The Cloudwatch service provided by AWS can achieve monitoring and observability. It provides data to monitor applications deployed in the AWS account. The same monitoring data can optimize resource utilization and get an insight into the application’s health. You can use Cloudwatch to set alarms, get alerted, visualize logs and metrics, take automated actions, and discover insights to keep your applications running smoothly.
Example
You can get alerted when there are changes in your security Group, i.e., create an alarm triggered when configuration changes in AWS security groups. You can also monitor Console sign-in failures and get alerted when AWS Management Console sign-in attempts are unsuccessful.
AWS Security Best Practice 7: Always Use Encryption
A cryptographic key is needed to perform any kind of encryption. Managing this key is, again, a challenging task. AWS KMS(Key Management Service) makes creating and managing cryptographic keys easy. It also controls its use across various AWS security services and applications.
AWS KMS is a fully managed, Centralized Key Management AWS Service. It is a single control point to manage cryptographic keys. One can easily create, import, delete, rotate, and execute permissions on keys using KMS. KMS helps to boost AWS Security.
AWS Security Best Practice 8: Implement the Right Cloud Security Framework
There are specific policies, tools, rules, and configurations needed to manage the security of a cloud platform. AWS Cloud Security Frameworks outline these security standards and organizational guidelines. Cloud Security Frameworks list functions important to manage cybersecurity-related risks in a cloud-based environment. Cloud Security Frameworks provide a structure and methodology to help avoid damaging security incidents.
Speaking about AWS, AWS Cloud infrastructure and services have been validated against the NIST 800-53 Revision 4 controls, PCI DSS Level 1 Service Provider and have been awarded CIS Security Software Certification for CIS Benchmark(s).
Now, let’s look at these frameworks.
PCI-DSS (Payment Card Industry Data Security Standard)
PCI-DSS(Payment Card Industry Data Security Standard) aims to enhance global payment account data security by developing standards and supporting services that drive education, awareness, and practical implementation by stakeholders. It promotes standards in the Payment Card Industry for the safety of cardholder data globally. PCI-DSS guides maintaining payment security and sets technical and operational requirements for organizations accepting or processing payment transactions.

NIST (National Institute of Standards and Technology)
NIST (National Institute of Standards and Technology)is part of the U.S. Department of Commerce and is committed to safeguarding personal privacy.
It provides a set of standards and guidelines for security controls for information systems at federal agencies. NIST also provides a framework for Improving Critical Infrastructure Cybersecurity. To ensure sufficient protection of integrity, confidentiality, and availability of information, the Federal Information Systems typically must go through a formal assessment.
The NIST Cybersecurity Framework (CSF) is supported by governments and industries worldwide as a recommended baseline for any organization.
CIS (Center for Internet Security)
CIS (Center for Internet Security) is a non-profit organization working independently to make the cyber world safer for people, businesses, and governments. It provides best practices for securing IT systems and data on the Internet. It works on developing, validating, and promoting the best method to protect people, businesses, and governments against cyber threats on the Internet.
CIS offers various programs, tools, memberships, and services to secure organizations. Some of CIS’s offerings are MS-ISAC, CIS Controls, CIS Benchmarks, and CIS CyberMarket.
AWS Security Best Practice 9: End-to-end Encryption
End-to-End encryption is a method to encrypt the communication and secure it from third parties.
TDE, Transparent Data Encryption, encrypts stored data on DB instances and is supported by AWS RDS for SQL Server (SQL Server Enterprise Edition) and Oracle (Oracle Advanced Security option in Oracle Enterprise Edition). TDE encrypts data automatically before it is written to database or storage and decrypts when it is read from the database or storage. This kind of encryption is used when it is vital to encrypt sensitive data. TDE improves cloud security and helps store sensitive data encrypted on AWS Cloud.
AWS Security Best Practice 10: Penetration Testing
The last AWS cloud security practice is that AWS permits its users to carry out Penetration Tests on certain services in their accounts.
The user must abide by the policies set by AWS for such tests. You can carry out pen-tests on your AWS account by following the policies and guidelines at Penetration Testing. You don’t need any approval from AWS to carry out pen-tests against your account. Also, contracted third parties can perform security assessments that do not violate the policy defined by AWS.
Permitted services for Penetration Testing:
- Amazon EC2 instances, WAF, NAT Gateways, and Elastic Load Balancers
- Amazon RDS
- Amazon CloudFront
- Amazon Aurora
- Amazon API Gateways
- AWS AppSync
- AWS Lambda and Lambda Edge functions
- Amazon Lightsail resources
- Amazon Elastic Beanstalk environments
- Amazon Elastic Container Service
- AWS Fargate
- Amazon Elasticsearch
- Amazon FSx
- Amazon Transit Gateway
- S3 hosted applications (targeting S3 buckets is strictly prohibited)
Prohibited activities for Penetration Testing:
- Route 53
- Denial of Service
- Port flooding
- Protocol flooding
- Request flooding (login request flooding, API request flooding)
Customers can not perform Denial Of Services(DOS), and if they want to perform DDOS(Distributed Denial Of Services), they should review the DDoS Simulation Testing policy of AWS.
You can also take a look at our slideshow about top AWS services to learn more about AWS security.
AWS security Case Studies for top FSI customer
Coinbase
Coinbase is a secure platform used to buy and sell cryptocurrencies. It supports cryptocurrencies like Bitcoin, Ethereum, Bitcoin Cash, Litecoin, etc. It is headquartered in San Francisco and is the first regulated bitcoin exchange in the United States. The company’s core tenets are security, scalability, and availability.
Crypto exchange hacks have existed since the origin of the first crypto exchanges, and some are so prominent that they leave a dent in the industry’s integrity. But Coinbase is still secured from these hacks.
According to Witoff, Director at Coinbase, Security is the most important of these tenets. Coinbase wanted to have their platform on something that would work for them with uncompromising security. After evaluating multiple cloud vendors, Coinbase was confident in Amazon Web Services (AWS) and started designing the new Coinbase Exchange using AWS IAM(Identity and Access Management ) and RDS, EC2, Lambda, S3, and a few other services.
The result is that Coinbase can now store its customers’ funds securely using AWS.
AWS Services used by Coinbase are:
- Amazon Elastic Compute Cloud (Amazon EC2)
- Amazon Simple Storage Service (Amazon S3)
- Amazon Relational Database Service (Amazon RDS)
- Amazon Kinesis
- Amazon Elastic MapReduce (Amazon EMR)
- AWS Lambda
- AWS Identity and Access Management (IAM)
- AWS CloudTrail
Starling Bank
Starling Bank is a digital bank based in the United Kingdom. It is a regulated and fully licensed bank built to give people a fairer, more competent, secure, and strict humane alternative to the traditional banks. Making sure that customers’ data stays free from cyber-attacks and fraud was one of Starling’s goals, which was to provide the best banking service in the world.
Starling also had to remain compliant. AWS was an obvious choice for Starling as it was clear to the UK and EU industry regulators that all of the technology would be secure and compliant as standard.
The result is, Starling Bank has built a successful Mobile-Only Retail Bank on AWS.
AWS Services used by Starling Bank are:
- Amazon Elastic Kubernetes Service (Amazon EKS)
- AWS Lambda
- Amazon Relational Database Service (Amazon RDS)
- Amazon Simple Storage Service (Amazon S3)

Conclusion of AWS Security Best Practices
As per Gartner, “through 2025, 99% of cloud security failures will be the customer’s fault.” Security is a shared responsibility between AWS and its customers. You can trust AWS as it has proven itself to be a strong Cloud partner. However, you should verify. Financial organizations can take advantage of AWS Services that maximize their agility by using the existing compliance measures and security standards.
Also, by following AWS Security Best Practices and Cloud Security Standards, you can build a more secure environment to host your applications. Most of the time, misconfiguration and improper access practices are responsible for data breaches and illegitimate access.
To ensure AWS Security, implement the right security tools according to your app.
FAQs
AWS is highly secure, employing robust measures including: Physical Security, Network Security
Access Control, Compliance, Monitoring and Logging.
Also, AWS follows a shared responsibility model where AWS secures the infrastructure, and customers secure their data and applications within AWS.
Cloud Security is the practice of protecting the Cloud Environment, applications deployed, and data stored on the Cloud by following the set of best practices. It involves the procedure and services that secure the Cloud Environment from internal and external cyber-attacks on the Cloud Environment and its applications.
While making the transition to the Cloud, it is imperative to ensure that the data and applications deployed on the Cloud are not compromised. Cloud Environment provides excellent services, flexibility through remote working, scalability, fast data sharing, etc. Moreover, securing the data and applications, i.e., Cloud Security, is of utmost importance as sensitive business information and intellectual property may be exposed through accidental leaks.
Security Groups, Cloudtrail, WAF, GuardDuty, are a few of the top AWS Security features.
You can improve AWS Security in the following ways.
1.Enable limited and required network access using Security Groups.
2.Take action on actionable findings in your AWS accounts by GuardDuty.
3.Maintain Cloudtrail and Cloudwatch logs as logging and monitoring are essential parts of the security plan.
4.Additionally, enable Multi-factor Authentication(MFA) to protect accounts from illegitimate access.