Are you worried about the security of your data in the Cloud? The answer lies in AWS Cloud Security Tools. With the rapid adoption of the Cloud, businesses face a pressing need to safeguard their digital assets from an ever-expanding array of cyber threats. This is especially important for healthcare organizations, which must abide by stringent industry rules like the HIPAA (Health Insurance Portability and Accountability Act) and manage sensitive patient data.
This raises a crucial question: How can organizations effectively protect their sensitive data and assure compliance in the cloud? AWS Security tools are the reason we’re here.
Imagine having a full range of Security Tools in AWS that are specially made to protect your cloud infrastructure, control user access, identify and address risks, encrypt data, and uphold compliance. Talking about the healthcare industry, maintaining the confidentiality and privacy of patient information is crucial. These organizations require strong security solutions to manage user access, identify and reduce risks, encrypt data, and guarantee regulatory compliance. This is where AWS Cloud Security Tools come into play.
In this blog, we’ll take a deep dive into the realm of AWS Cloud Security Tool, exploring its features and functionalities that are particularly relevant to healthcare organizations. We’ll look at 12 Security Tools in AWS that focus on important areas like Identity and Access Management, Threat Detection and Continuous Monitoring, Network and Application Protection, Data Protection, and Compliance with regard to threats. Gaining awareness of these powerful AWS Security Monitoring Tools will enable you to implement efficient security measures and guarantee industry regulations are followed.
- AWS Well-Architected Framework
- Categories of AWS Security, Identity, and Compliance Service
- AWS Security Tools for Healthcare Organizations
- Achieving Security and Compliance with AWS in Real-World
- Summary
- Conclusion
- FAQs
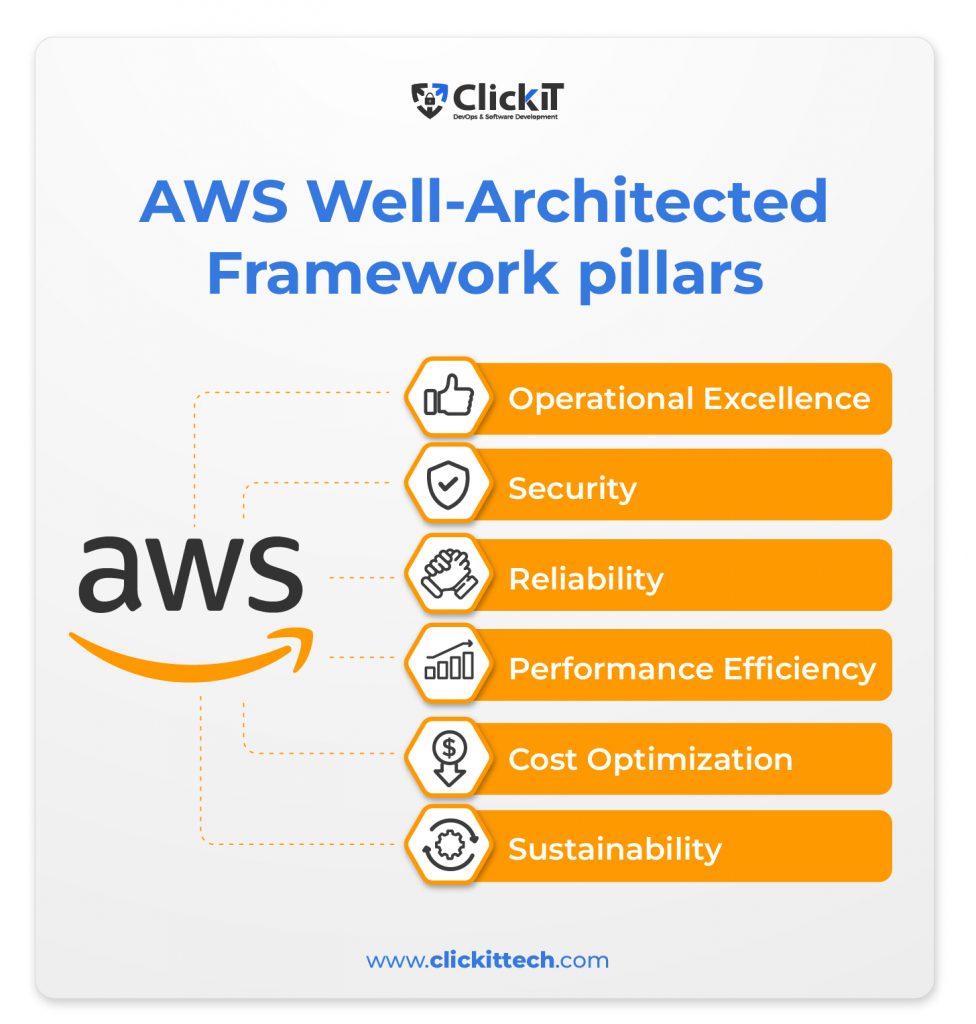
AWS Well-Architected Framework: A Blueprint for Secure Cloud Architectures
Organizations can use the AWS Well-Architected Framework to further improve their cloud security in addition to the robust AWS Cloud Security Tools. This framework offers a collection of best practices and architectural principles to design, create, and optimize secure, high-performing, robust, and effective cloud-based solutions. You can use it to continuously compare your architectures to best practices and pinpoint areas for improvement.
By incorporating the AWS Well-Architected Framework into your security strategy, you can make sure that your cloud architecture is planned and executed in a way that prioritizes security while also considering other crucial factors like performance, cost-effectiveness, and operational efficiency. Building secure and reliable cloud architectures is guided by the framework’s six pillars, which are as follows:
- Operational Excellence:
The ability to support development and manage workloads successfully, get insight into their operations, and continuously enhance supporting processes and procedures to generate business value are all aspects of the Operational Excellence pillar. - Security:
The ability to safeguard data, systems, and assets is a component of the security pillar that enables you to use cloud computing to enhance your security. - Reliability:
The Reliability pillar includes a workload’s capacity to carry out its intended task correctly and consistently at the anticipated time. This comprises having the capacity to manage and test the workload over its entire lifecycle. - Performance Efficiency:
The capacity to employ computing resources effectively to fulfill system needs and to sustain that effectiveness as demand shifts and technologies advance is a component of performance efficiency. - Cost Optimization:
The ability to operate systems to provide business value at the lowest price point is a component of the cost optimization pillar. - Sustainability:
The Sustainability pillar focuses on how the environment is affected, particularly how much energy is used and how effectively it is used.
By aligning with these six pillars of the AWS Well-Architected Framework, organizations can build cloud architectures that are secure, reliable, cost-effective, and environmentally sustainable.
Now that we have gained an understanding of the AWS Well-Architected Framework let’s delve into the next section and explore the Categories of AWS Security, Identity, and Compliance Services.
Categories of AWS Security, Identity, and Compliance Services
AWS offers a comprehensive array of services that address various aspects of security, identity, and compliance when it comes to protecting your cloud infrastructure. These services are divided into the following categories.
Identity and Access Management (IAM)
IAM, one of the foundational AWS Cloud Security Tool categories, manages user identities and their access to AWS resources. It gives you precise control over who can access and interact with your AWS environment by enabling you to establish and manage users, groups, roles, and permissions. IAM enables you to put the principle of least privilege into practice by allowing users to have only the permissions essential for their tasks.
With AWS, you have access to the identity management services, tools, and capabilities you need to get started quickly while securely managing access to your workloads and apps as you scale.
Threat Detection & Continuous Monitoring
The goal of the Threat Detection & Continuous Monitoring category is to continuously monitor your AWS environment for any signs of potential security risks. You can quickly discover security incidents with the help of these services, which provide real-time insights into the security status of your resources.
It is a crucial step in the security lifecycle and can be used to support a quality process, a legal or compliance need, as well as efforts to identify and counter threats. There are several strategies we are going to discuss in the upcoming blog that you can employ in AWS when dealing with detective mechanisms.
Network and Application Protection
Securing your network infrastructure and applications that leverage AWS is the main emphasis of this category. It consists of services that offer defense against network-level attacks, Distributed Denial of Service (DDoS) attacks, and vulnerabilities in web-based applications. You can create secure network boundaries, filter and track network traffic, and protect your applications from potential dangers by putting these services into place.
AWS caters to the specific compliance and protection needs of your network and application security teams. You can get granular protections at the host-, network-, and application-level boundaries using AWS network and application protection services.
Data Protection
In the cloud environment, data protection is crucial, and AWS provides several services to help you protect your data. To guarantee the privacy, availability, and integrity of your data, these services offer encryption tools, data backup and recovery services, and secure storage alternatives. AWS data protection services assist you in upholding compliance and safeguarding your sensitive data, whether the data is being protected at rest or while it is in transit.
With AWS, you can change the privacy settings for your data and have complete control over its usage, accessibility, and encryption.

Compliance
For organizations working in different industries, maintaining regulatory compliance is essential. In order to assist you in adhering to industry-specific compliance standards like PCI DSS, HIPAA, GDPR, and others, AWS provides a variety of services and features. These AWS Cloud Security Tools offer the controls, records, and auditing tools required to prove compliance and preserve a secure and reliable environment.
Discover the Top 10 Best AWS Security Practices for Financial Services
Companies can dramatically improve their AWS infrastructure’s security, identity management, and compliance by utilizing the AWS Security Tools in these categories.
We will go deeper into each area in this blog, examining the important AWS Security Tools and their functions, as well as talking about the advantages, use cases, and pricing factors that apply in the real world.
Before that, let’s quickly understand the need for security tools in AWS for Healthcare Organizations.
AWS Security Tools for Healthcare Organizations: Ensuring Data Protection and Compliance
Data security and regulatory compliance are crucial in the healthcare sector. To protect sensitive patient data and adhere to stringent rules like the Health Insurance Portability and Accountability Act (HIPAA), healthcare organizations must use strong security measures. The AWS Security Tools upcoming in this blog support organizations in adhering to HIPAA compliance regulations while helping to maintain the privacy, security, and availability of healthcare data. With the help of these AWS Security Tools, healthcare organizations can create a compliant and secure cloud architecture, safeguarding patient data and reducing the possibility of security breaches.
Continue reading more about the Most Important HIPAA Compliance AWS Services.
Healthcare organizations can concentrate on providing patients with high-quality treatment while feeling confident in the security and compliance of their AWS environment by using an AWS Security Tool.
Now, let’s dive into the actual tools and explore how AWS Cloud Security Tools can help not only healthcare organizations but anyone on AWS achieve data protection and compliance.
You can discover more AWS services in our video.
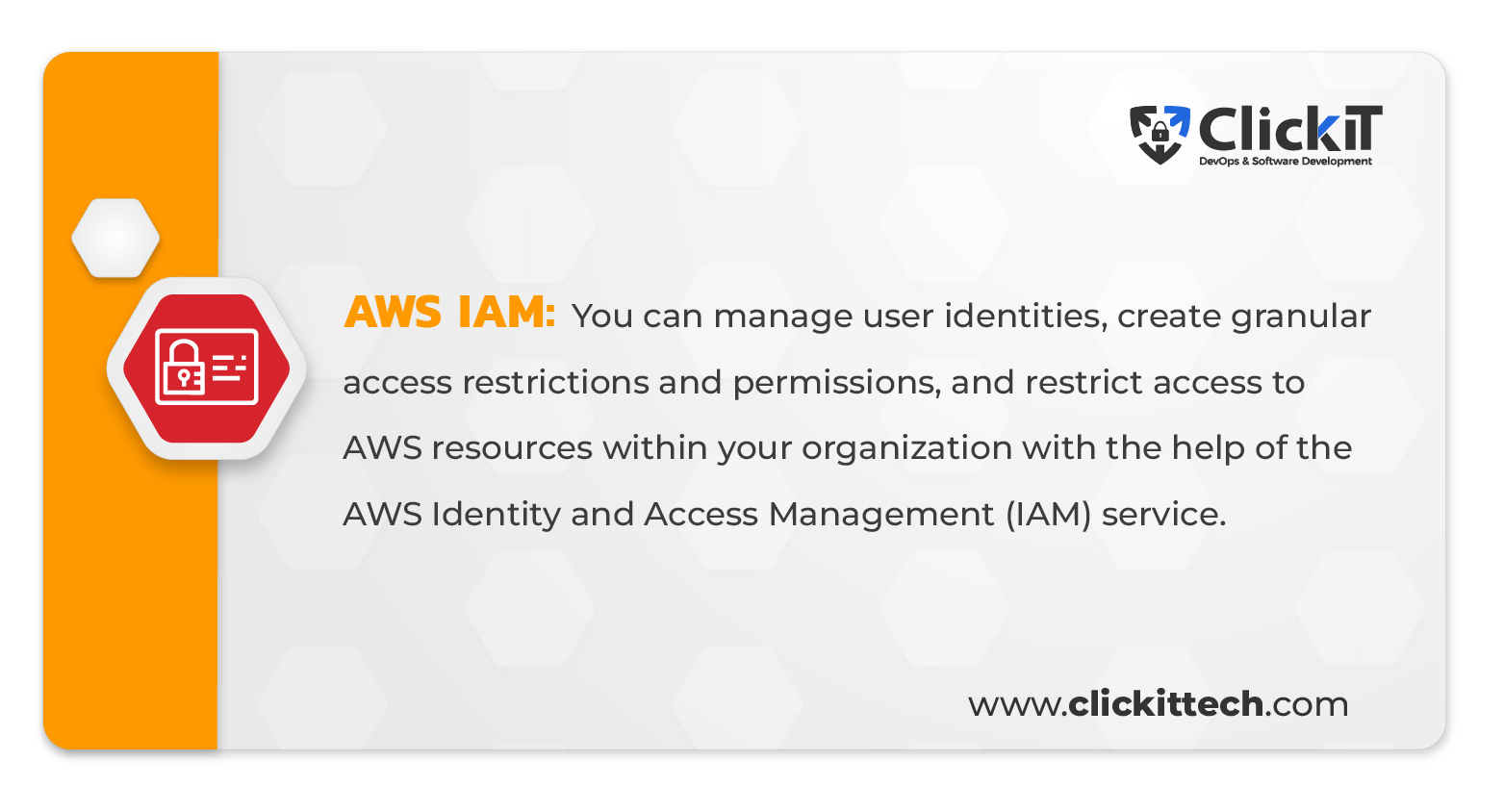
AWS IAM: Identity and Access Management
You can manage user identities, create granular access restrictions and permissions, and restrict access to AWS resources within your organization with the help of the AWS security tool Identity and Access Management (IAM) service. A secure foundation for your AWS infrastructure may be created using IAM by centralizing the management of user credentials, roles, and permissions.
Features of IAM
- Fine-grained access control
Using IAM’s fine-grained access control, you can set exact permissions for particular users, groups, or roles. - Delegate access by using IAM roles
You can grant users, programs, or services access to AWS resources using IAM roles instead of having to distribute permanent access keys. - IAM Roles Anywhere
You may now utilize IAM roles to grant secure access to resources outside of AWS, such as third-party applications or on-premises systems, thanks to this capability. - IAM Access Analyzer
IAM Access Analyzer helps identify resources within your organization and accounts that are shared with external entities, validates IAM policies against policy grammar and best practices, and can generate IAM policies based on the access activity recorded in your AWS CloudTrail logs. - Permissions guardrails
IAM enables you to create guardrails around permissions, ensuring that users have the permissions needed to carry out their duties. - Attribute-based access control
Attribute-based access control (ABAC) is an effective authorization strategy that allows you to create granular permissions based on specific user attributes like department, job role, or team name.
Pricing model of IAM
You don’t have to pay for using IAM. It comes free of cost. Get the most out of the Cloud, and get ready to meet all the AWS Benefits.
Amazon GuardDuty: Threat Detection & Monitoring
AWS provides Amazon GuardDuty, a powerful threat detection and monitoring service. It continuously scans your AWS environment for potential risks and malicious activity while analyzing and monitoring activity. GuardDuty offers real-time alerts and insights by utilizing machine learning and anomaly detection techniques, enabling you to react to security issues and safeguard your valuable assets.
Features of GuardDuty
- Threat detection
By identifying and warning you of potential dangers, such as unauthorized access attempts, compromised instances, or unusual API requests, GuardDuty helps improve your AWS infrastructure’s security posture. - Continuous monitoring across AWS accounts
Your AWS account and workload event data available in AWS CloudTrail, VPC Flow Logs, and DNS Logs are continuously monitored and analyzed by Amazon GuardDuty. - Threat severity levels
Three severity categories (Low, Medium, and High) are provided by Amazon GuardDuty to assist you in deciding how urgently to respond to potential threats. - Threat response and remediation
Automated security responses to security findings are supported by Amazon GuardDuty.
Pricing model of GuardDuty
The pricing for GuardDuty is determined by the amount of service logs, events, workloads, or analyzed data. The cost may vary depending on the data source and AWS Region. Click here to know the pricing in detail.
AWS CloudTrail: Threat Detection & Monitoring
Amazon Web Services (AWS) offers the powerful tool AWS CloudTrail, which enables you to track, log, and retain account activity within your AWS environment. It gives you thorough information about the operations carried out on your AWS resources, assisting you in gaining visibility and command over your infrastructure.
Every API call performed within your AWS account is recorded by CloudTrail, which provides a thorough audit trail of activities.
Features of CloudTrail
- Event History
By default, CloudTrail keeps a thorough record of all API requests made over the previous 90 days. You can look into and examine events inside your AWS account over a certain period using this historical data. - Multi-Region Support
You can record API activity across various AWS regions using CloudTrail’s multi-region trails feature. - Multi-account
AWS CloudTrail’s multi-account capability allows businesses to enable and control CloudTrail logging across multiple AWS accounts from a single location. - Management and Data Events
AWS CloudTrail’s Management Events and Data Events functionalities offer in-depth analyses of the activity taking place within an AWS environment.
Pricing model of CloudTrail
CloudTrail pricing is determined by the number of events recorded and the storage utilized for log files. The cost is calculated based on these factors, ensuring that you are billed accordingly for the volume of events and the storage space required to retain your log data. Click here to know the pricing in detail.
Amazon CloudWatch: Threat Detection & Monitoring
AWS security tool Amazon CloudWatch is a comprehensive solution for threat detection and monitoring. It offers a centralized platform for gathering and examining logs, analytics, and events from different AWS services and applications. CloudWatch provides real-time insights into your AWS environment’s performance, health, and security by combining data from several sources.
Features of CloudWatch
- Collect
You may quickly gather and store logs from your resources, apps, and services using Amazon CloudWatch for more than 70 AWS services. - Monitor
Applications that span multiple accounts within a Region can be monitored and troubleshooted with the aid of CloudWatch. You can define a metric threshold and an action trigger in Amazon CloudWatch. - Act
You can automate capacity and resource planning with the aid of CloudWatch. An automated Auto Scaling operation can be triggered by setting an alarm threshold for a key metric. - Analyze
With 15 months of metric data available through Amazon CloudWatch, you can track trends and seasonality while also performing historical analysis to optimize resource use. - Compliance and Security
Because Amazon CloudWatch and AWS Identity and Access Management (IAM) are connected, you can manage which resources and users can access your data and how they can access it.
Pricing model of CloudWatch
With no commitment upfront or minimum payment restrictions, CloudWatch offers flexible pricing. You can only pay for the exact services you use. The cost depends on a variety of elements, including Data Transfer OUT from CloudWatch Logs, Metrics, Dashboards, Alarms, Events, and other features it provides. Click here to know the pricing in detail.
AWS Security Hub: Threat Detection & Monitoring
AWS Security Hub is a thorough cloud security service that performs automated and continuous inspections for security best practices across your AWS services. It’s one of many AWS security monitoring tools that assist you in identifying misconfigurations and collect your security alerts or discoveries in a consistent style.
Features of Security Hub
- Security and compliance checks
To evaluate the adherence to security best practices and compliance standards of your AWS services, Security Hub runs automated checks against them. You can find vulnerabilities, security threats, and misconfigurations with its assistance. - Managing security alerts
Security Hub collects security alerts, also known as findings, from multiple AWS services and integrated AWS Partner Network (APN) security solutions. You can effectively manage and prioritize these discoveries because it gives you a centralized view of them. - Automation and response
For your security operations to run more efficiently, Security Hub enables automated workflows and response mechanisms. You can define custom actions, set up event-driven security workflows, and automate the response to security incidents.
Pricing model of Security Hub
Security Hub adopts a pricing structure based on three primary factors: the number of security checks performed, the volume of finding ingestion events, and the number of rule evaluations processed on a monthly basis. Click here to learn more about the pricing in detail.
AWS WAF: Network and Application Protection
The AWS WAF (Web Application Firewall) is a powerful security service created to secure your web applications running on AWS’s network and apps. It helps defend your apps from widespread web vulnerabilities like SQL injection, cross-site scripting (XSS) attacks, and others. You can give your web applications extra security and ensure their availability, integrity, and confidentiality by including AWS WAF in your architecture.
Features of WAF
- Web traffic filtering
You may use AWS WAF to filter and evaluate incoming web traffic based on a variety of factors, such as IP addresses, locations, and HTTP headers. - AWS WAF Bot Control
You can identify and reduce automated bot traffic that could be damaging to your web apps with the help of this feature, safeguarding the resources used by your application and enhancing performance. - Account Takeover Fraud Prevention
By providing sophisticated detection and mitigation capabilities, AWS WAF helps prevent account takeover fraud, as AWS WAF can spot suspicious activity patterns and stop unauthorized access attempts. - Account Creation Fraud Prevention
You can put procedures in place to identify and stop the creation of fraudulent accounts by utilizing AWS WAF. - Real-time visibility
Real-time visibility into the traffic entering your web apps is provided by AWS WAF. You may monitor and examine traffic patterns, spot abnormalities, and learn more about potential dangers. - Integration with AWS Firewall Manager
AWS WAF fully integrates with AWS Firewall Manager, allowing you to centrally manage and implement firewall rules across many accounts and resources. - Full feature API
You can programmatically manage and set up your web application firewall with AWS WAF, thanks to the extensive API it provides.
Pricing model of WAF
The pricing for AWS WAF is determined by several factors, including the number of web access control lists (web ACLs) you create, the quantity of rules added per web ACL, and the volume of web requests received. With AWS WAF, there are no upfront commitments. Click here to know the pricing in detail.
AWS Shield: Network and Application Protection
Amazon Web Services (AWS) offers AWS Shield, a fully managed Distributed Denial of Service (DDoS) protection service. It is made to protect your resources and applications from the constantly changing DDoS attack threat scenario. By guaranteeing your network’s and apps’ availability and dependability with AWS Shield, you can concentrate on your primary business processes without worrying about DDoS attacks.
Features of Shield
- AWS Shield Standard
All AWS customers have free access to the built-in DDoS protection feature known as AWS Shield Standard. It offers automatic defense against the most typical and often seen DDoS attacks.
- AWS Shield Advanced
AWS Shield Advanced is an improved DDoS protection service that goes above and beyond what Shield Standard can give in terms of features and advantages. In addition to access to a 24/7 DDoS AWS Shield Response Team (SRT) for individualized support during attacks, it offers superior DDoS protection for more complex and sophisticated attacks.
Customized detection based on traffic patterns, automatic mitigations for attacks targeting your applications, complete visibility into DDoS attacks with near real-time notification, and cost protection to safeguard against scaling charges resulting from DDoS are a few of the key features of AWS Shield Advanced.
Pricing model of Shield
Shield Standard is offered without charge and is bundled in by default for all AWS clients. However, you are charged for Data Transfer Out Usage for Shield Advanced. Click here to learn more about the pricing.
AWS VPN: Network and Application Protection
AWS Virtual Private Network (AWS VPN) creates a private and secure connection from your network or device to the AWS Cloud. You can connect to AWS resources from a client or extend your current on-premises network into a VPC. AWS VPN provides two private connectivity options, both of which have the high availability and strong security your data needs.
- AWS Site-to-Site VPN:
AWS Site-to-Site VPN is a service that allows you to securely connect your on-premises network to your Amazon Web Services (AWS) Virtual Private Cloud (VPC). It establishes an encrypted connection over the Internet using the IPSec protocol, creating a secure communication channel between your on-premises data center or network and your VPC.
- AWS Client VPN:
On the other hand, AWS Client VPN is a managed VPN service provided by AWS that enables you to securely access your AWS resources and resources in your VPC from remote locations. It allows individual users to establish a secure VPN connection to their VPC using OpenVPN-compatible clients.
Features of VPN
- Secure connectivity:
The traffic is encrypted by the TLS encrypted, TLS VPN tunnel protocol used by AWS VPN. - High availability:
High availability capabilities, such as redundancy and automated failover choices, are available with AWS VPN. - Private IP VPN:
Your on-premises network and your VPC can connect over a private IP VPN using AWS VPN. - Monitoring:
AWS CloudWatch offers monitoring capabilities using AWS VPN. - Authentication:
Different authentication techniques are supported by AWS VPN to guarantee secure access to your VPN connections. - Authorization:
Access to your VPN resources can be restricted with the help of AWS VPN’s authorization features.
Pricing model of VPN
You are charged for each VPN connection hour that your VPN connection is provided and accessible using an AWS Site-to-Site VPN connection to your Amazon VPC. And in the case of AWS Client VPN, you are charged for the number of active client connections per hour and the number of linked subnets with Client VPN per hour. Click here to know more about the pricing in detail.
AWS Certificate Manager: Data Protection
For your applications and resources operating on AWS, Amazon Web Services (AWS) offers ACM. This service streamlines the process of provisioning, managing, and deploying SSL/TLS (Secure Sockets Layer/Transport Layer Security) certificates. You can supply certificates directly with ACM or by importing third-party certificates into the ACM administration system for your integrated AWS services.
Features of Certificate Manager
- Centrally manage certificates
You may easily centrally manage your SSL/TLS certificates with the help of AWS Certificate Manager (ACM). By looking at your AWS CloudTrail logs, you may also audit how each certificate was used. - Secure key management
When securing and maintaining private keys, best practices in key management and strong encryption are employed. - AWS service integration
ACM smoothly integrates with other AWS services, making it simple for you to provision certificates and link them to your resources. - Import third-party certificates
The deployment of SSL/TLS certificates generated by third-party Certificate Authorities (CAs) is made simple by ACM. When an imported certificate is about to expire, you can keep track of the expiration date and import a replacement.
Pricing model of Certificate Manager
Using AWS Certificate Manager to manage SSL/TLS certificates is free of charge. Click here to know in detail
AWS Secrets Manager: Data Protection
Amazon Web Services (AWS) provides an excellent data security service called AWS Secrets Manager that enables secure administration and storage of secrets, including API keys, database passwords, and other delicate credentials. Organizations may quickly store, cycle, and recover secrets with Secrets Manager, preserving their integrity and confidentiality.
Features of Secrets Manager
- Secure secrets storage
Secrets Manager uses robust encryption and secure storage techniques to protect secrets at rest and in transit. Secrets are encrypted and kept in a separate Secrets Manager vault using the AWS Key Management Service (KMS). - Automatic secrets rotation
Secrets Manager’s capability to automate the rotation of secrets is one of its primary advantages. Secrets can be set up to rotate based on established policies or at regular intervals automatically. - Automatic replication of secrets to multiple AWS Regions
The ability to automatically replicate secrets across several AWS Regions is provided by AWS Secrets Manager, ensuring high availability and disaster recovery readiness. - Programmatic retrieval of secrets
Secrets Manager offers a safe and user-friendly API interface that enables programmatic secret retrieval. - Audit and monitor secrets usage
Comprehensive auditing and monitoring tools for secret usage are provided by the Secrets Manager. Organizations can manage and keep track of who accesses what secrets, when it happened, and from where. - Compliance
AWS Secrets Manager can be used to satisfy compliance obligations. - Integration
The secure retrieval and use of secrets in apps and infrastructure are made possible by Secrets Manager’s easy integration with a number of AWS services which enables runtime secret retrieval for apps through Secrets Manager.
Pricing model of Secrets Manager
You pay for Secrets Manager based on the volume of stored secrets and API requests. There are no long-term commitments or up-front fees. Simply put, you pay for usage. Click here to know the pricing in detail.
AWS KMS: Data Protection
The Amazon Web Services (AWS) Key Management Service (KMS) is a managed service that enables customers to create and maintain encryption keys to safeguard their data and resources. You can easily generate, store, and manage encryption keys with this safe and scalable service, allowing you to encrypt and decrypt data within your AWS environments.
Features of KMS
- AWS service integration
You may quickly encrypt data at rest with KMS’s seamless integration with a number of AWS services, including Amazon S3, Amazon EBS, Amazon RDS, and Amazon Redshift. - Secure
Nobody, not even AWS staff, will be able to retrieve your plaintext keys from the AWS KMS service. To safeguard the integrity and confidentiality of your keys, the service uses hardware security modules (HSMs) that are regularly validated. - Asymmetric keys
You can build and use asymmetric KMS keys and data key pairs with the aid of AWS KMS. An encryption key pair or a signing key pair can be chosen for use with a KMS key. - Client-side encryption
To safeguard data directly within your application on AWS, as well as in hybrid and multi cloud scenarios, you can use AWS KMS with client-side encryption libraries. Before storing data in AWS services or any other storage medium and third-party services of your choice, you can use these libraries to encrypt it.
Pricing model of KMS
All KMS keys you generate, as well as monthly API queries made to the service, are charged to you. Click here to know more in detail.
AWS Artifact: Compliance
You can access and download compliance reports, agreements, and other key documents related to your AWS environment’s security and regulatory compliance using the AWS Artifact service offered by Amazon Web Services (AWS). It streamlines the process of proving compliance to auditors and regulatory agencies by acting as a central repository for crucial compliance paperwork, including AWS ISO certifications, Payment Card Industry (PCI) reports, and Service Organization Control (SOC).
Features of Artifact
- Compliance Reports
Access to numerous compliance reports, such as AWS ISO certifications, Payment Card Industry (PCI), and System and Organisation Control (SOC) reports, is available via AWS Artifact. - Agreements
Users can browse and download a variety of agreements, including Non-Disclosure Agreements (NDAs) and Business Associate Agreements (BAAs) for HIPAA compliance.
Pricing model of Artifact
You are not charged for using the AWS Artifact documentation or agreements.












Achieving Security and Compliance with AWS in Real-World
In this section, we’ll look at practical examples of how to comply with HIPAA and PCI in AWS environments, emphasizing the security tools and best practices that may be used to do so.
AWS Security Tools Use Case 1: HIPAA Compliance
Scenario
In this use case, a healthcare organization that uses AWS infrastructure must comply with the Health Insurance Portability and Accountability Act (HIPAA). The company must adhere to the strict security and privacy guidelines specified in HIPAA in order to maintain and process sensitive patient data.
Success Story
We can be motivated by Lira Medika‘s success story as we work to achieve HIPAA compliance. An Indonesian healthcare provider named Lira Medika needed to make sure that their AWS environment complied with this regulation. They aimed to adhere to strict privacy and security standards while securely storing and processing patient health details.
Lira Medika used several AWS Security Tools and services to achieve HIPAA compliance. Here is a summary of how they used these tools to satisfy their compliance obligations:
- WAF:
WAF helped to protect web applications and APIs from common web-based attacks. - CloudTrail
CloudTrail allowed them to monitor and log all API activities within the AWS environment. - S3:
S3 provided a way to back up patient health records and encrypt the data in transit and at rest. - RDS:
RDS enabled encrypting and storing patient health records data at rest.
AWS Security Tools Use Case 2: HIPAA Compliance
Scenario
In this use case, we’ll look at how healthcare technology provider Ultrasound.ai partnered with ClickIT for a Full Product Development and used AWS Cloud Security Tools to secure data security and compliance in their cloud infrastructure.
Success Story
In their pursuit of compliance and data protection, Ultrasound.ai confronted numerous difficulties. They required a secure and scalable infrastructure to manage the difficulties of integrating four APIs and a cutting-edge AI model, keep infrastructure costs down, and create the core application features. Additionally, because they were a healthcare organization, they had to go by strict standards, such as HIPAA, which mandated that they put in place strong security measures and guarantee the confidentiality, integrity, and accessibility of patient data.
To address these challenges, Ultrasound.ai sought the vast expertise of ClickIT in the healthcare software development domain. To create and deploy a robust security architecture on AWS, ClickIT collaborated closely with Ultrasound.ai, by implementing DevOps Security Best Practices.
After the project is finished, the customer now has access to an application that allows them to view the source images, enter their clinical impressions in a HIPAA-compliant manner, and receive forecasts created by UAI.
To help Ultrasound.ai with a secure and compliant cloud environment, ClickIT used several AWS Security Tools.
- IAM:
IAM helped establish granular access controls - ACM:
ACM was used for managing and deploying SSL/TLS certificates - CloudTrail:
CloudTrail allowed logging and auditing API activity
- CloudWatch:
CloudWatch helped monitor and detect security incidents in real-time
AWS Security Tools Use Case 3: PCI Compliance
Scenario
In this use case, we’ll take a look at a situation in which a business must achieve Payment Card Industry Data Security Standard (PCI DSS) compliance for its AWS environment. This business must maintain the security and protection of cardholder data because it processes credit card transactions.
Success Story
CardFlight is a top supplier of the tools and technology that enable developers to create their own mobile point-of-sale systems. Being fully compliant with Payment Card Industry (PCI) standards for data storage and management was one of CardFlight’s challenges. Companies must ensure that all systems are physically secure and encrypt all personal information and credit card data collected from clients at the point of sale, both in flight and at rest. All system and process modifications must also be completely documented and subjected to frequent audits.
CardFlight used a number of AWS cloud security tools and services to overcome these challenges and achieve PCI compliance. Here is how these tools aided them in their quest for compliance:
- VPC:
VPC allowed the creation of a logically isolated section of the AWS cloud, providing secure and private network connectivity for the resources. - IAM:
IAM allowed to establish granular access controls, ensuring that only authorized individuals could access sensitive data. - KMS:
KMS helped manage encryption keys to protect personal details and credit card information. - CloudTrail:
CloudTrail provided a comprehensive audit trail of API activity within the AWS account.
AWS Security Tools Conclusion
When it comes to the security of organizations, especially healthcare organizations, AWS offers a wide range of security tools and services to meet diverse security needs. With so many options available, selecting the right ones for your specific requirements can be challenging.
That’s why we have curated a list of 12 top AWS security tools, handpicked and experienced by our experts, to help you navigate through the abundance of options and establish a secure and compliant environment to safeguard patient data and meet regulatory requirements such as HIPAA.
These carefully chosen tools have shown to be quite effective in tackling a variety of security concerns, including threat detection, data protection, compliance, identity and access management, and more. You can strengthen the security of your AWS environment and protect your priceless data and resources by utilizing these AWS security tools.
However, it’s important to remember that in addition to the tools listed above, AWS also provides a full array of AWS security monitoring tools. Visit the AWS Security products page here if you’re looking for more AWS cloud security tools or want to check into further possibilities.
Alternatively, if you would like specialized support and direction in selecting and putting the appropriate security tools into place for your AWS environment, especially your healthcare app environment, please don’t hesitate to contact us.
This blog is also available on Medium
AWS Security Tools FAQs
To improve the security and compliance of your cloud infrastructure, Amazon Web Services (AWS) offers a complete range of services and features known as AWS Security Tools. These solutions offer a wide range of functionalities, including data encryption, network protection, threat detection, identity and access management, and more.
There are various advantages to using AWS Security Tools, including:
-Improved security against data breaches and online threats.
-More control and visibility over user access and permissions.
-Streamlined adherence to rules relevant to a given industry.
-Automated threat monitoring and detection.
-Data protection and encryption key management become easier.
-Pay-as-you-go pricing for security solutions that are affordable.
Your particular security needs and the structure of your workloads will influence the AWS security tools you use. Among the frequently used AWS security monitoring tools are:
-IAM, which controls user access and permissions, is one of the most widely used AWS security tools.
-Amazon GuardDuty for Threat detection and ongoing monitoring.
-AWS WAF for defending online applications against common vulnerabilities.
-KMS for keeping track of encryption keys.
-CloudTrail, used to log and audit AWS API activities.








