Companies around the world have adopted agile and different application development methodologies that leverage the work for different departments or areas. But in this new Agile and DevOps world where everybody on a team is involved in their application’s rapid change and evolution, we must promote accountability for everybody regarding security. This is when DevSecOps tools and processes join the party. But what is DevSecOps?
Table of contents
- What is DevSecOps?
- Why is DevSecOps important?
- What are the main benefits that you gain when implementing DevSecOps?
- How can I enable DevSecOps on my current DevOps pipeline or SDLC?
- What tools and processes you need to enable in your DevSecOps process?
- What is the ideal workflow for DevSecOps?
- What are the challenges when enabling DevSecOps?
- In the end
What is DevSecOps?
DevSecOps is an innovative model that provides everyone on a team with accountability for implementing security in the application. From planning, design, development, and QA/Testing to release and operating in a production environment.
When implementing DevSecOps on the Software Development Lifecycle (SDLC), an organization will experience continuous integration and will notice that the costs for compliance are reduced. This is because code is constantly being analyzed, tested, delivered, and released properly.
Why is DevSecOps important?
In this rapidly changing era, everything is evolving at a very accelerated pace. We continue to discover vulnerabilities and breaches across platforms and operating systems. Patches are released constantly. But, being a part of the operating team of a company, one can’t afford the risk of having a vulnerability on any side of the IT system/application.
What are the main benefits of implementing DevSecOps?
- Prevents vulnerabilities present in your code.
- Reduces the number of ways to exploit your application.
- Minimizes downtime.
- Improves your application stability, availability, and security.
How can I enable DevSecOps on my current DevOps pipeline or SDLC?
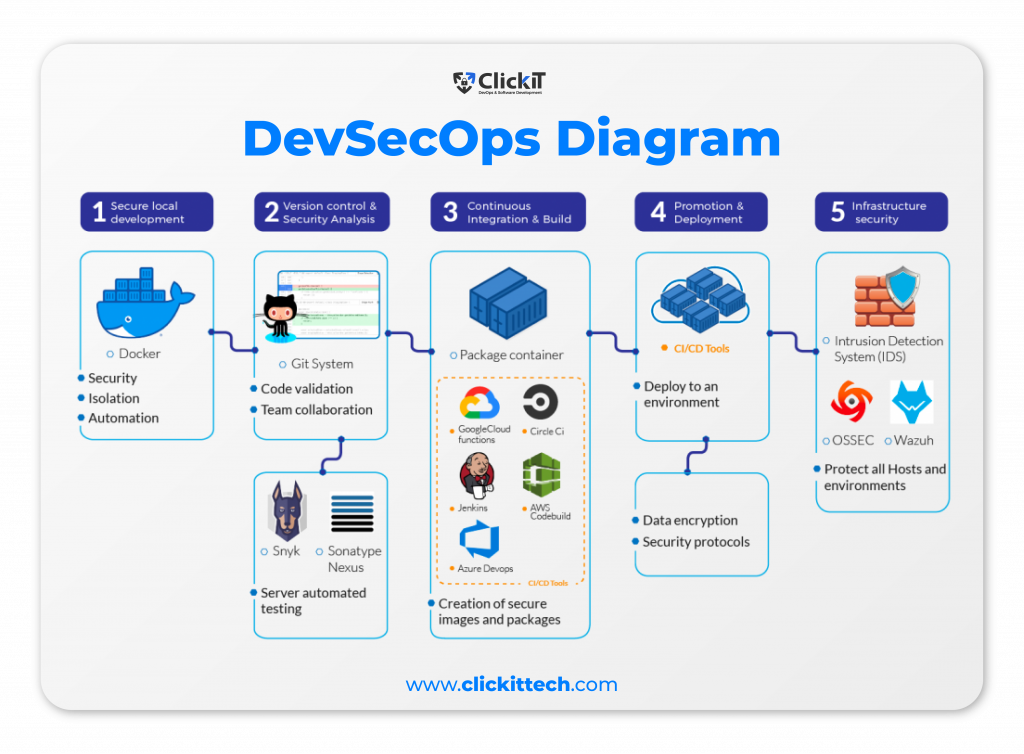
Five important phases must be followed to enable DevSecOps on a current DevOps pipeline or in the Software Development Lifecycle.
DevOps has brought big benefits for enterprises, and so will DevSecOps. Here are the crucial phases to enable DevSecOps on your SDLC:
Phase 1: Secure local development
Start by implementing secure working environments (Local Secure Environments). When developing an application, you can use Open Source technologies in most cases. Docker is a great helper in this phase since it automates the infrastructure and service deployments of local machines. So, when using this ready-to-go docker environment, ensure you use the most recent/updated versions of the Docker Images and scan them for vulnerabilities. Even the images from official providers have vulnerabilities that need to be patched.
Phase 2: Version Control and Security Analysis
Enable Vulnerability while uploading your source code. Having multiple hands or people working on a piece of code can lead to vulnerabilities, especially when they are remote. Git systems have greatly improved collaboration between team members and code. When a team member uploads a piece of code, I strongly suggest that you enable automated testing for security on your code dependencies and core; some good alternatives to do it are Snyk or Sonatype’s Nexus.
Phase 3: Continuous Integration & Build
When creating the development image/package, you’ll need to ensure that your build tool or system has the proper security in place; it uses https:// protocol, is properly hardened and secure, is available and protected for attack mitigation, or is even not accessible via the internet. You can use tools like Jenkins, Circle CI, AWS CodeBuild, Google Cloud Functions, and Azure DevOps.
Phase 4: Promotion & Deployment
When deploying to an environment, insert the environment variables through your CI/CD tool and try to manage them as secrets. Proper encryption and management of these are recommended in order to enhance your security protocols.
Phase 5: Infrastructure security
When your app is deployed, make sure that you have an IDS (Intrusion Detection System). Tools like OSSEC or Wazuh will help protect all your hosts on this matter.
Once your code gets to production, it doesn’t mean that it will be 100% secure. New vulnerabilities are disclosed daily, but this cycle will help you and your team test your code against all the repositories of known vulnerabilities when monitoring, configuring, reconfiguring, adapting, and deploying solutions.
What tools and processes do you need to enable in your DevSecOps process?

What is the ideal workflow for DevSecOps?
a. A developer creates a new code and integrates it into the VCS.
b. Members from the QA team retrieve the code to perform the static code analysis to identify security flaws or functional tasks.
c. A test environment is created automatically using IaC, such as Terraform, Cloudformation, Chef, or Puppet, and the security configurations are added to the system.
Have trouble choosing between Terraform and Cloudformation? Read the blog to make your decision.
d. The test automation suite is performed on the application with a tool, usually Selenium or any other tool that performs Backend, UI, Integration, Security, and API tests.
e. After the test suite is performed and successful, the new changes are sent to the production environment.
f. The new code version will now be monitored in the production environment using an APM or Cloud-native monitoring tool.
Following these points, you ensure that your application follows TDD practices, improving code quality and compliance, increasing the number of code releases to production, and reducing the time to market, which is essential for any organization.
What are the challenges when integrating DevSecOps tools?
1. Enabling too many tools
Using too many tools can become a problem on your SDLC, especially when your team is not used to working with DevOps or security tasks. The main recommendation here is to start slow. Start by enabling only the necessary tools to familiarize your team with the process, and add more when you feel your team is prepared for it.
2. Getting used to the methodology
It will take some time for the team to get used to the DevSecOps methodology/culture and keep following it to comply with the norms that your business demands. Try always to stay up-to-date and coach your team for the newest technologies.
Resources like courses, books, and online coaching platforms can facilitate continuous learning and ensure your team remains well-versed in the latest technologies.
3. Chasing perfection in the process
Remember that the DevSecOps process will never be perfect but will mature over time. Teams always try to chase perfection, leading to more problems with even more integrations or dependencies.
What is DevSecOps: Conclusion
Ultimately, every organization must try to work with DevSecOps tools or processes and develop a multidisciplinary team focusing on security. That’s how an organization will allow all its collaborators to have accountability on the part they are actively developing. Hopefully, you found this blog about what is DevSecOps interesting. Leave a comment below and tell me your opinion.

FAQs about what is DevSecOps
DevSecOps is an extension of DevOps that integrates security practices throughout the software development lifecycle. While DevOps focuses on collaboration between development and operations, DevSecOps incorporates security as an integral part, ensuring that security measures are implemented from the start rather than as an afterthought.
DevSecOps processes emphasize shifting left, integrating security early in development, automating security checks, and fostering a culture of shared responsibility. This proactive approach helps identify and address security issues sooner in the development pipeline.
Several tools support DevSecOps practices like OWASP Dependency-Check for scanning dependencies, Docker Security Scanning for container security, and SonarQube for continuous code quality and security inspection. These tools help automate security checks and ensure code integrity throughout the development lifecycle.