DevOps security is a set of best practices that integrate security processes, people, and DevOps security tools into the development pipeline, enabling organizations to deliver software in a secure environment continuously.
Whether you call it DevSecOps, network security, cyber security, DevOps and security, security compliance, or just hardening the cloud infrastructure, security is a critical component in today’s dynamically changing cloud environments.
Video of the Top 5 DevOps Security Best Practices
- What is DevOps Security?
- The architecture of DevOps Security
- DevOps Security Best Practices
- Security Compliance Regulations
- CyberSecurity Frameworks
- Conclusion
- FAQs
What is DevOps Security?
DevOps combines developers and operations teams to coordinate and contribute seamlessly to software development projects. DevOps Security is about integrating security into the CI/CD pipeline to deliver applications and services quickly.
However, now that businesses have started noticing the amazing results of DevOps-enabled organizations, they are aggressively embracing it. Today, DevOps integrates every department into cross-functional teams, making every team member responsible for the entire lifecycle of an application or service.
Different Types of IT Security
Information technology security can be classified into the following types:
- Information Security: A process of protecting information against unauthorized access, cyber-attacks and malware.
- Hardening IT: A security measure that reduces the surface of system vulnerabilities.
- Penetration Testing: A security method that simulates a cyber attack on a system to identify any exposed vulnerabilities.
- Vulnerability Assessments: A process of reviewing the security weaknesses of a system in a systematic way.
- DevSecOps: A method that integrates security with development and operations teams, thus sharing security responsibility throughout a product’s lifecycle.
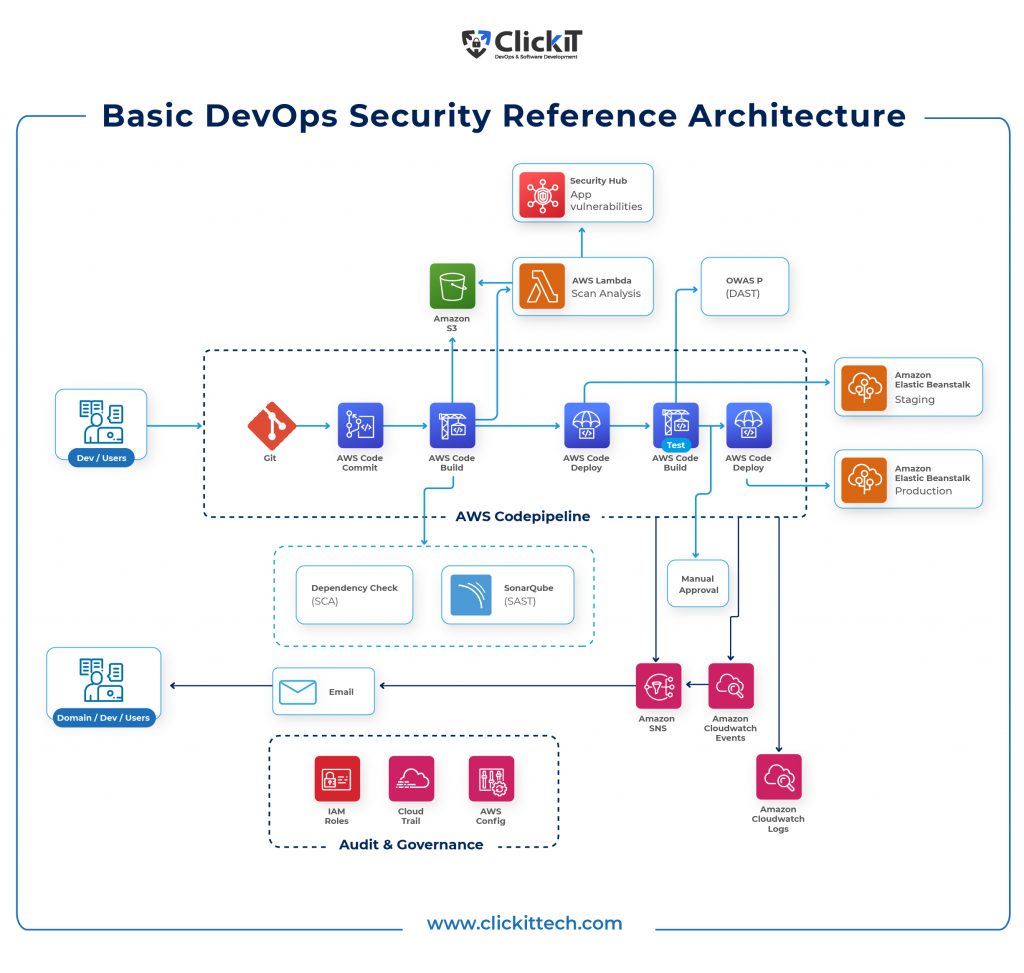
The Architecture of DevOps Security
DevOps Security Best Practices
- Hardening your IT Resources
- Mitigate Common DDoS Attacks
- Cloud Security
- Host and Network Firewall
- Intrusion Monitoring System
- Encryption Everywhere
- A Backup System for Disaster Recovery
- Security Audits
- VPN Service for your VPC Network
- Constantly Update your Software, Framework, and Libraries
- DevSecOps
DevOps Security Best Practice # 1: Hardening your IT Resources
By reducing the attack surface, administrators can minimize potential flaws exploited by hackers. In addition to providing a higher level of security, hardening your systems improves system functionality and simplifies audit and compliance tasks.
First, you must secure your operating system and Nginx/PHP servers. If you’re using containers, secure everything within the container. For a cloud instance, secure the software and services running inside the instance. Secure special services, such as Jenkins, as well.
Server and OS
In addition to a strong password policy, multi-factor authentication and AES encryption, we recommend applying the latest updates and patches from the OS developer and enabling security technology features. Other methods include privilege-based access, restricting peripherals connected to the server, host drive encryption, secure boot, biometrics, and updating drivers and deleting unnecessary ones. Whether you use LAMP (Linux – Apache HTTP Server – MySQL – PHP ) or MERN (MongoDB – ExpressJS – ReactJS – NodeJS), make sure to secure all servers, apps and services involved in the project.
Securing your JavaScript
Cross-Site Scripting (XSS) is a common security vulnerability in JavaScript environments. Address another important vulnerability: Cross-Site Request Forgery (CSRF). In addition, do your best to eliminate browser plugin code vulnerabilities, sandboxing issues, and client-server trust relationship issues. Regarding Node.js, check for Command Injection and SQL Injection issues.
Most common attacks on Linux systems happen on an unsecured kernel. Even though the kernel possesses an in-built defense system, it’s important to effectively secure the kernel by frequently applying security patches, enabling secure boot Full or Thorough Mode, implementing kernel module signing and loading rules, enabling kernel lockdown, hardening the Sysctl.conf file etc. You also need to implement strict permissions and perform ongoing monitoring.
Network
Network hardening includes firewall configuration and security with iptables or ufw, network traffic encryption, removal of unnecessary services, protocols, open ports, access lists, and securing remote access points. We highly recommend network segmentation. This involves breaking down a network into multiple subnets or segments so that you can monitor these smaller networks using granular policies.
An Internet gateway can access a public subnet, while a private subnet remains inaccessible from the Internet. You should place your databases and Redis servers in the private subnet and all other resources in the public subnet. We recommend using virtual private networks for sensitive traffic.
Also, Secure Socket Shell (SSH) enables public-key-based authentication and facilitates encrypted connections between two endpoints in a network. We highly recommend generating SSH keys for accessing containers and servers. Cpanel and Bitnami deploy multiple third-party software/services you don’t need. This is why we do not recommend deploying your SaaS applications with graphical admin interfaces like Cpanel, WHM, bitnami and Plesk. Finally, Fail2ban is a powerful IPD framework that can help you mitigate bot attacks.
Containers
When it comes to container security, restrict network port accessibility, limit the image size and build data and use network segmentation to deploy containers in different subnets, based on the data they operate. Try executing one process per container. Furthermore, be careful when sharing host namespaces and limit containers from acquiring new privileges.
DevOps Security Best Practice # 2: Mitigate Common DDoS Attacks
A content delivery network (CDN) helps you accelerate your application delivery speed, deliver content faster, and increase your SaaS application performance. Cloudflare is a popular CDN that offers globally distributed servers to improve application performance with reduced load times.
Cloudflare facilitates superior app performance by caching and serving static files from the nearest location. A notable feature is the developer mode, which lets you turn off the caching option when making changes to your application. CDN Cloudflare is free, easy to set up and integrates seamlessly with existing infrastructure.
Cloudflare CDN also has a security functionality, which acts as an intermediary between the end-user and applications and thereby mitigates common DDoS attacks and malicious web attacks, combining DevOps and security.
Cloudflare offers useful apps that help you deliver a superior user experience. Moreover, the in-depth analytics features provide clear insights into website performance. With CDN, Web Application Firewall and DDoS, Cloudflare is a comprehensive platform that runs your applications in a secure environment with optimal performance. The free version allows you to use the CDN and other interesting features. On the other hand, upgrading to a paid version allows you to leverage the web application firewall feature.
DevOps Security Best Practice #3: Cloud Security
Protecting your workloads with identity theft protection, as well as data and user accounts is important by implementing Cloud security, and in this case, we will focus on AWS security best practices.
- Limit access to AWS resources using the Identity and Access Management (IAM) system. An IAM system comprises users, groups, roles, credentials, and policies. Applying policies to groups instead of individual users allows you to quickly manage security while gaining visibility into network operations.
- Assign a root user: the user who created the AWS account and the email associated with it. As such, the root user has more privileges than an administrator and can make or break the entire system. Therefore, only use the root user account in exceptional circumstances.
- Rotate the access keys: if you use access keys instead of IAM roles, regularly rotate the access keys at least every 3 months using the IAM credentials report.
- Amazon Key Management System (KMS): a fully managed encryption tool to efficiently manage keys for AWS resources.
- An AWS security group: is a virtual firewall that controls the outbound and inbound traffic for EC2 instances. AWS virtual private clouds come with a default security group. Depending on the protocols and ports, you can add policies and rules to each security group that govern the entire VPC or certain resources within the VPC.
- Multi-factor authentication: is an easy way to protect your devices from unauthorized access. Ensure that the AWS console, which is a web app that enables you to manage AWS resources, is MFA-enabled.
- AWS Virtual Private Network (VPN): To securely connect to on-premise, remote, and client devices, use the solutions available in two forms: AWS Client VPN and AWS Site-to-Site VPN. While the client VPN connects end users with AWS resources, AWS Site-to-Site VPN connects Amazon VPCs with your network.
DevOps and Security Best Practice #4: Host and Network Firewall
A firewall shields your device and network to protect them from malicious or unwanted traffic. They can be configured to block specific apps, data, ports, locations based on IPs, and more. Firewalls can be hardware devices or software programs.
Network Firewall
A network firewall is installed between the Internet and the protected LAN for the purpose of filtering traffic. Network firewalls are mostly hardware devices. A notable network firewall is Amazon Security Group.
Amazon Security Group
It is a virtual firewall that filters traffic to your AWS resources. When a virtual private cloud is created, AWS creates a default security group. You can configure the security group to protect each VPC or each resource in the VPC. The traffic is filtered based on port numbers and protocols. Amazon Security Group also helps you control traffic to your cloud network, specifically to EC2 instances.
Host Firewall
It is typically a software program installed on the host machine to protect the individual host device. Host firewalls offer mobility but are difficult to scale. That said, setup is easy. We recommend having a network firewall and a host firewall, as a second level of defense.
IPtables
It is a DevOps security tool and a Linux firewall that enables administrators to filter malicious and unwanted traffic and redirect packets to alternate ports and IPs while protecting the system against DDoS attacks. Iptables is a Linux firewall that provides the lowest level of access to the Linux kernel, thus making it the most reliable and robust firewall on the market. You can easily configure and control this versatile utility from the command line.
While the rich feature set is an advantage for advanced users, beginners will have to go through a learning process. Iptables have been deprecated. However, the underlying netfilter is still in operation, and the user interface for the Netfilter is now offered as nftables.
UFW
or uncomplicated firewall, is another Linux firewall built on iptables but simplifies iptables usage complexities. You need a deep knowledge of TCP/IP and expert knowledge of the kernel to effectively use iptables. UFW makes it easy to configure and use firewalls. ConfigServer Security and Firewall is a server security firewall that controls server traffic tracks network connections and prevents DDoS attacks. It can be easily managed via a web interface or a secure shell.
CFW or Convergent Firewall
It is a comprehensive product that combines multiple converged security solutions, including a secure web gateway, a data center firewall (DCFW), a Gi/SGi integrated with Carrier Grade NAT (CGN) and DDoS, an IPSec site-to-site VPN with a centralized management console that efficiently manages SDN, as well as Cloud and NFV environments. That said, it comes with a price tag.
DevOps Security Best Practice #5: Intrusion Monitoring System / Threat Intelligence System
Intrusion Detection System (IDS)
It is a network security solution that assists administrators in detecting network vulnerabilities. It listens to traffic and reports the results to administrators. On the other hand, an Intrusion Prevention System (IPS) takes things one step further by not only detecting malicious network attacks but also preventing them.
Moreover, a threat intelligence system gathers information about known threats and possible cyber attacks with the objective of analyzing and building effective mechanisms to help organizations effectively combat and mitigate these threats. The IDS/IPS DevOps security tools can use this information to identify and block traffic from any specific source, such as an IP address.
Amazon GuardDuty
It is an intelligent threat detection service from AWS that offers organization-wide visibility into suspicious activities and malicious traffic. This IDS/ DevOps security tool continuously monitors your AWS accounts and workloads and automatically triggers responses when a threat is detected, thus helping you mitigate threats as soon as possible.
Wazuh
It is a popular, highly scalable open-source AWS DevOps security tool that combines Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) functionalities to detect and prevent most types of threats quickly. Furthermore, Wazuh is free to use and comes with a rich feature set including vulnerability detection, intrusion detection, incident response, security analytics, log data analysis, file integrity monitoring, configuration assessment, regulatory compliance and more.
Indeed, Wazuh allows you to use a single DevOps security tool for ID/IPS and threat intelligence tasks. It also integrates easily with third-party solutions. As such, small and medium-sized organizations can highly benefit from the cost savings that come with Wazuh.
AWS CloudTrail
Although not an intrusion detection system, AWS CloudTrail is a DevOps security tool with log-recording and API call monitoring service by Amazon. You can configure it to work with SIEM and XDR tools, making audit and compliance easy and effective.
If your organization uses AWS, we recommend using GuardDuty and CloudTrail. If your organization doesn’t use AWS, Wazuh is a good choice. You can also use Elastic Stack (ELK), which comes with ElasticSearch, Logstash, and Kibana.

DevOps Security Best Practice #6: Encryption Everywhere
These days, encryption is no longer an option but rather a necessity. The idea is to encrypt everything and anything that can be encrypted. When it comes to website encryption, we recommend using HyperText Transfer Protocol Secure (HTTPS). HTTPS extends the regular HTTP protocol by using the Transport Layer Security (TLS) protocol to encrypt the communication.
First, identify all API calls, services, and web servers hosted in the cloud, a remote location, or on-premise that require encryption. Then, obtain relevant certificates from a commercial certificate authority, such as Comodo Code Signing. Secondly, the SSL certificates are installed, HTTPS encryption is configured, and web servers are enabled to use HTTPS. In addition, be sure to administer and monitor encrypted websites continuously. Encrypt ports range from 80 to 443.
AWS Certificate Manager (ACM)
It is another handy tool from Amazon that governs the complex tasks of creating, storing, deleting and managing private and public SSL/TLS certificates for your AWS resources. You can import certificates into the ACM system from third party sources or have them directly issued from the ACM.
Amazon Key Management Service (KMS)
This tool is designed to create, delete, and manage cryptographic keys across all AWS services used in the infrastructure. It offers a centralized dashboard that defines and controls usage policies from a centralized view. You can access AWS KMS via the KMS CLI, SDK, or AWS IAM dashboards. Additionally, AWS manages it fully, handling security, maintenance, and infrastructure availability.
Encrypt log files
- To ensure greater protection for logs, encrypt log files so that hackers won’t be able to edit them without the encryption key. For encryption purposes, you can use CloudWatch, which encrypts log group data by default, or Amazon KMS to encrypt log data.
Amazon EBS encryption
- Use Amazon EBS encryption to encrypt the EBS resources of your EC2 instances. It uses Amazon KMS to automatically encrypt volumes and snapshots during the creation stage and manage them. It also allows you to define custom encryption policies.
Amazon Secrets Manager
- Amazon Secrets Manager is a powerful service that manages your secrets, API keys and database credentials throughout their life cycles. It allows you to access data using fine-grain policies, safely rotate secrets and centrally audit, all while only paying for the number of secrets managed in the system.
Always encrypt API calls
- Ensure that all data traveling between the API server and the user is encrypted. For REST APIs that use HTTP protocol, you must implement the TLS protocol to encrypt REST API communications and web pages.
DevOps and Security Best Practice #7: A Backup System for Disaster Recovery
Disaster recovery is one of the DevOps security best practices that helps protect and preserve data. AWS Backup is a perfect place to centralize data management and automate data protection across all AWS services in the infrastructure. It’s a fully-managed and user-friendly service that allows you to easily backup all types of data from a single pane. The data is stored in S3 buckets by default. You can also easily define backup policies and retention periods depending on your workload requirements.
Finally, AWS Backup automates the entire process for all services with backup policies for each service. All of this being said, the only downside is that you are required to pay for the cost of snapshot storage.
Snapshots.
First off, it’s important to note that snapshots are different from backups. Elastic Block Store (EBS) is a point-in-time snapshot which references data stored in the storage volume while the backup performs write activities to the live storage volume. It is a read-only snapshot which helps admins restore data when need be. Automated EBS snapshots also permit you to capture backup at the same point in time which allows for crash consistency.
When it comes to backing EC2 instances, AWS offers multiple options. EBS volume is a block-level storage device that acts as a physical hard drive when attached to an EC2 instance. EC2 instances use EBS volume by default for persistent storage.
Infrastructure as Code
Another solution is to implement Infrastructure as Code (IaC), wherein the infrastructure is managed via scripts stored in a central repository. Terraform and CloudFormation are the two most popular IaC tools available on the market.
When the infrastructure is managed as code and stored in a repository, using Bitbucket, GitHub or AWS Code Commit, will grant you the luxury of versioning the infrastructure. As such, not only can you automate infrastructure provision, but you can also instantly relaunch a previous version of deployment in the event of a disaster.
DevOps Security Best Practice #8: Security Audits – Vulnerability Assessments
A security audit assesses an organization’s information system against audit checklists, government regulations, and industry security best practices. The audit covers the software, applications, physical components, network vulnerabilities, and how employees collect and manage data. As a general rule, it is recommended that you audit your cloud infrastructure, as well as vulnerability assessments and misconfigurations in your applications and infrastructure at least once every quarter.
Amazon Inspector
It continuously scans AWS workloads to identify and quickly resolve security issues. The tool integrates easily with AWS Security Hub, Event Bridge and container-based workloads. It automatically discovers EC2 instances and ECR-based container workloads and assesses the security status.
Moreover, when a workload configuration change occurs, it automatically rescans the image. Amazon Inspector comes with a configuration scanning and activity monitoring engine and a built-in content library of reports and rules. Finally, it can be configured through an API enabling security implementation in DevOps environments.
AWS Config
It is another handy DevOps security tool for inventory management and asset tracking in cloud-based AWS environments. This tool helps administrators identify why a resource or service isn’t working properly.
It uses Amazon SNS to notify admins of configuration changes along with the details of the IP address and the person requesting the change. You can check the recorded historical resource configurations using a CLI, SDK or AWS management console. When integrated with AWS CloudTrail, AWS Config allows you to gain deep insights into API calls.
Technologies for threat intelligence.
First off, Wazuh is a good option. Then we have OSSEC, another host-based IDS system. OSSEC is an open-source tool with a cross-platform architecture that enables administrators to monitor different systems from a central dashboard. The tool offers comprehensive IDS services, including rootkit monitoring, windows registry monitoring, log analysis, integrity checking, time-based alerting, and more.
DevOps Security Best Practice #9: VPN Service for your VPC Network
A virtual private network (VPN) is a security measure that transmits data between a remote server and the end-user machine via an encrypted tunnel and thereby shields your data from hackers and unauthorized access. It also helps with safe browsing by masking the IP address and browsing activity.
AWS offers a VPN service called AWS Client VPN. It’s a fully managed VPN service that allows remote users to access AWS resources and workloads securely. It automatically scales up on-demand and offers advanced authentication features. AWS Client VPN also offers the flexibility of connecting to the cloud from any location. Finally, the high availability of AZs is a useful advantage.
OpenVPN is another popular VPN service that offers interesting features. OpenVPN is a site-to-site or point-to-point VPN service developed by James Yonan in 2001. The tool is written in C language and uses the TLS protocol and OpenSSL encryption library to facilitate secure communications in remote facilities and bridged/routed configurations.
DevOps Security Best Practice #10: Constantly Update your Software, Framework, and Libraries
The first thing you need to keep updated is your operating system. Apply patches and updates regularly. Regarding Windows OS, Microsoft offers the System Center Configuration Manager (SCCM), a feature-rich tool for deploying patches to stateful servers. SCCM comes with an annual licensing fee. If you want a free option, Windows Server Update Services (WSUS) may be exactly what you need.
Linux patching is easy compared to Windows. Zypper, YUM, and Apt are popular patch management tools for Linux distributions. Also, Amazon offers the AWS System Manager Patch Manager, which automatically scans your Linux and Windows instances and applies patches. AWS System Manager enables administrators to view and manage the IT infrastructure on AWS. Patch Manager is a feature of System Manager that performs patch management for operating systems and applications. It covers VMs, on-premise devices, and a fleet of EC2 instances and edge devices.
You only need to pay regular EC2 instance charges for AWS SMPM, and there is no additional charge. The tool uses existing Windows and Linux OS update methods and the same AWS SDKs and AWS CLI. This means you can use the same frameworks for patching that you use for automation jobs and scripts.


Bonus DevOps Practice: DevSecOps
You should have a thorough understanding of the concept and work with a good CI/CD pipeline and the right DevOps security tools before embracing DevSecOps.
DevSecOps aims to bring security into the DevOps CI/CD pipeline, making it a shared responsibility throughout the product life cycle.
In traditional development environments, security is incorporated at the final stage of development and managed by an isolated team. However, this outdated approach is inefficient in DevOps environments wherein software is developed in smaller units incrementally using microservices and cloud-native architectures. By integrating security to the left of the DevOps pipeline, organizations can manage infrastructure and application security from day one.

Download our free ebook about the 10 Essential DevSecOps Practices.
Bonus DevOps Practice : Web Application Firewall
A Web Application Firewall (WAF) acts as a security shield between the Internet traffic and the web app, enabling organizations to monitor and filter data packets. You can use cloud-based, network or host-based WAFs installed as cloud services, network appliances or server plugins. WAFs are mostly deployed via reverse proxies.
While WAFs are useful for every business, they are especially important for organizations that process critical data. For instance, financial institutions that process sensitive card transactions can use a WAF to protect data and prevent information leakage. Moreover, WAFs help in complying with PCI CSS compliance. WAFs should be integrated with existing IDSs for comprehensive security monitoring. They come with features such as application profiling, customization of security policies, AI-based traffic pattern analysis, attack signature databases, DDoS protection, and CDNs.
AWS WAF
It is a popular cloud-native and on-demand web application firewall from Amazon. It’s a stable and highly scalable solution that is flexible enough to customize WAF rules and offers basic WAF features by default. The security features can be easily integrated with existing services. Furthermore, the technical support is good. However, it’s worth mentioning that the setup is slightly complicated, and AWS manages the WAF, which leaves users with minimal control over blocking.
Cloudflare WAF
It is another popular web application firewall that comes with rich features. You can configure it using APIs, and it offers good technical support. That said, documentation and integration with other services could be improved. Also, the WAF feature is only available for paid versions of Cloudflare.
While AWS WAF is more customizable, Cloudflare offers more automation. AWS WAF best suits teams with technical expertise, whereas Cloudflare aims for mass and consumer-grade markets.
Considering the above, AWS WAF is well suited for AWS-heavy environments. On the other hand, Cloudflare’s free version is good for CDN tasks, and its paid version can help with WAF tasks.
Bonus DevOps Practice: Enable Logging for Server, App and Cloud
This is one of the DevOps security best practices to improve security posture, gain better control over storage, analysis, and remediation tasks, enabling logging for servers, apps, and the cloud. By logging and monitoring API calls, organizations not only improve security and operational troubleshooting but also comply with industry regulations and audit purposes.
AWS CloudTrail
It is a popular logging and risk-monitoring service offered by Amazon. With this tool, users can seamlessly log, monitor and analyze all activities across the AWS infrastructure using AWS SDKs, management console, program line tools, and other services. AWS CloudTrail performs well regarding security analysis, operational issue troubleshooting, compliance, and data exfiltration.
CloudTrial
It is a web service that is automatically enabled when a free tier is created. The centralized log data is stored in an S3 bucket and events are delivered within 15 minutes of an API call. Best of all, CloudTrail is free, easy to implement and offers good support, including multi-language support. However, the interface could be improved and log analysis is complex.
Difference between CloudTrail and CloudWatch
CloudTrial is not to be confused with CloudWatch. While CloudWatch monitors apps and resources, CloudTrail monitors activities. CloudWatch is more popular for performance monitoring and offers higher-level monitoring of AWS apps and resources from multiple accounts. Data is retained for 15 days. Furthermore, CloudWatch offers static graphs and limited default graphs. All of this being said, it’s important to optimize costs when using this service, seeing as they quickly go up as you scale.
VPC Flow Logs
It is a useful feature of Amazon Virtual Private Cloud that allows users to monitor and analyze IP traffic through all network interfaces within the VPC. You can publish this log data to S3 buckets or CloudWatch logs to analyze traffic to instances or identify restrictive security group rules and determine the performance and security posture of apps as well as the AWS environment. However, VPC flow logs cannot capture the traffic of AWS DNS services, DHCP, as well as multiple IP addresses and legacy instances.
When it comes to application performance monitoring, New Relic and Datadog are two of the most popular DevOps security tools. Both come with an extensive ARM capability set and reporting features. However, New Relic is strong in monitoring apps, while Datadog excels in infrastructure monitoring. Both tools offer an intuitive web interface, are easy to use, and have good community support, API, and extensible. They also make it easy for third-party integrations and have good email security and website perimeter.
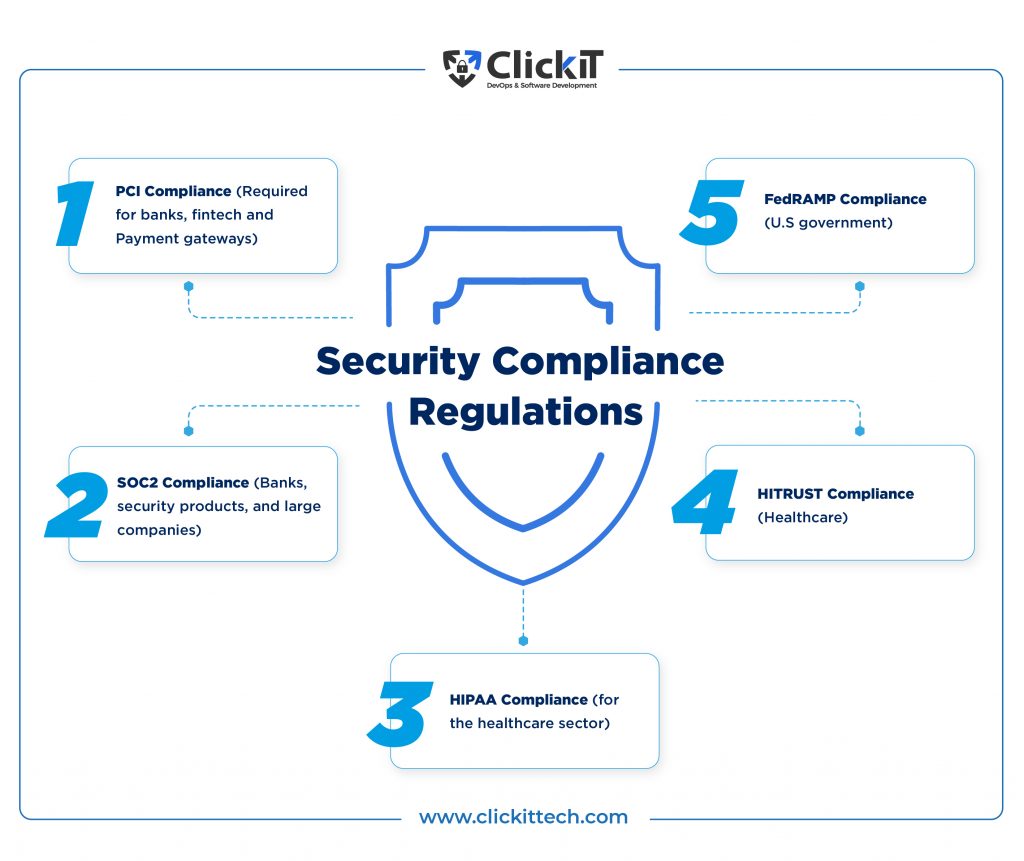
Security Compliance Regulations
1) PCI Compliance (Required for banks, fintech and Payment gateways)
PCI compliance requires all organizations that work with debit or credit cards to adhere to certain regulations to ensure they are operating in a secure environment. An independent body Security Standards Council (PCI SSC) comprising MasterCard, American Express, Visa, JCB and Discover manages and administers the enforcement of these regulations.
To comply with PCI regulations, organizations must ensure that the following requirements are met:
- Password Protection
- Firewall Protection
- Anti-Virus Protection
- Data Encryption
- Role-based Data Access
- Frequent software updates
- Physical Access restriction
- Access Logs
- Vulnerability Assessments
- Policy Documentation
For your information, AWS is a PCI DSS Level 1 Service Provider.

2) SOC2 Compliance (Banks, security products, and large companies)
SOC 2 is a security audit developed by the American Institute of CPAs that ensures a high level of information security for an organization. The audit is based on the five following trust principles:
- Security
- Privacy
- Availability
- Processing
- Confidentiality
SOC 2 compliance not only ensures that the highest information security practices are used but also gives a competitive advantage to organizations, seeing as they are very trusted by consumers. However, it’s a voluntary compliance standard.
3) HIPAA Compliance (for the healthcare sector)
The Health Insurance Portability and Accountability Act (HIPAA) is a regulatory standard that prescribes regulatory standards for the usage and disclosure of protected health information. It’s enforced by the Office of Civil Rights (OCR) and regulated by the Department of Health and Human Services (HHS). HIPAA applies to healthcare providers, health insurance providers, healthcare clearinghouses and businesses that encounter ePHI in their operations.
HIPAA regulations include:
- Policies, Procedures and Employee Training
- Self-Audits
- Remediation Plans
- Incident Management
- Documentation
4) HITRUST Compliance (Healthcare)
Health Information Trust Alliance (HITRUST) is a standardized framework that helps organizations demonstrate compliance with HIPAA. While this framework is designed to manage data, information security and compliance for healthcare organizations, it can be implemented in other sectors as well.
The HITRUST checklist includes:
- Defining protection information
- Understanding the movement of data across infrastructures
- Visualizing protected data volume
- Understanding the implications of data leaving the protected environment
- Reviewing system inventory
- Documenting everything
5) FedRAMP Compliance (U.S government)
FedRAMP stands for Federal Risk and Management Program. It’s a cybersecurity risk management program implemented by US federal agencies for purchasing and using cloud products and services. Organizations that intend to work with government agencies are required to comply with FedRAMP regulations.
FedRAMP’s authorization and compliance requirements are as follows:
- FedRAMP Documentation and FedRAMP SSP
- Plan of Action & Milestones Development (POA&M)
- Joint Authorization Board Provisional ATO
- Continuous Monitoring Program with vulnerability scans
FedRAMPthird party assessment (3PAO) assesses commercial cloud offerings. Moreover, AWS follows the FedRAMP process to obtain authorization for its cloud service products.

Conclusion
DevOps, coupled with microservices and cloud-native architecture, has changed how IT security operates. DevOps environments comprise hundreds of microservices, diverse sets of AWS DevOps security tools, code repositories, increased levels of automation, instantly spinning containers and shorter deployment cycles with rapidly changing configurations.
This goes to show that more services, tools and processes need to be protected. With the new risks and challenges involved, long-term security deployment strategies just don’t fit into the DevOps realm. These days, security should be integrated into development and operations processes at the beginning and throughout the product life cycle. Implementing these DevOps security best practices and the DevOps security tools are the best things you can do to keep your DevOps environments agile and secure.
FAQs
The most popular DevOps security tools include Synk, Amazon WAF, OSSEC, OWASP ZAP, Checkmarx, Veracode and Sonatype.
While Security DevOps practices for Azure are similar to that of AWS, the Azure infrastructure is tightly integrated with the Windows environment. As such, you can integrate Azure AD to leverage Windows offerings such as Active Directory Conditional Access Policy Validation for fine-grained access controls, restricting access to service accounts, right authentication method, Web Application Firewall and Microsoft anti-malware.
While both DevSecOps and cybersecurity share the common goal of enhancing security, their primary areas of application and scope differ significantly.
DevOps comes into play within the product development lifecycle, seamlessly integrating security measures throughout the entire process. On the other hand, cybersecurity extends its influence to various scenarios whenever digitalization is involved.
Hardening your IT Resources, Add a CDN Firewall such as Cloudflare to Mitigate Common DDoS Attacks, Host and Network Firewall.